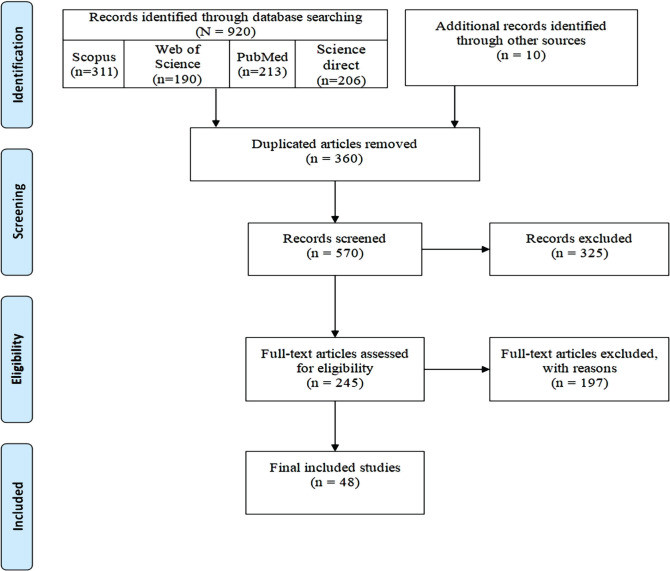
Cloud Technology In Healthcare is transforming how medical professionals manage and access patient data. At pioneer-technology.com, we delve into the security of cloud solutions, offering insights and strategies to ensure data protection. Secure cloud adoption is vital for modern healthcare, and understanding the risks and solutions is paramount.
1. What Is Cloud Technology in Healthcare, and Why Is It Important?
Cloud technology in healthcare involves storing and accessing health-related data and applications on remote servers instead of local hardware. This approach enables healthcare providers to enhance collaboration, reduce costs, and improve patient care through greater data accessibility and management.
Expanding on the Importance of Cloud Technology in Healthcare
Cloud technology offers significant advantages in healthcare, including:
- Enhanced Collaboration: Cloud solutions facilitate real-time data sharing among healthcare professionals, leading to better-coordinated care.
- Reduced Costs: Organizations can lower IT infrastructure costs by using cloud services.
- Improved Data Accessibility: Healthcare providers can access patient information from anywhere, improving efficiency and responsiveness.
- Scalability: Cloud platforms can scale resources based on demand, accommodating growing data volumes and user needs.
- Disaster Recovery: Cloud backups ensure data recovery in case of emergencies, safeguarding patient records.
The adoption of cloud technology is pivotal for modernizing healthcare and improving overall outcomes, making it essential for professionals and organizations to understand its potential and implications.
2. What Are the Key Benefits of Using Cloud Computing in Healthcare?
Cloud computing offers healthcare organizations increased efficiency, cost savings, and improved data management. Benefits include streamlined workflows, reduced IT infrastructure costs, and better access to patient information, leading to enhanced patient care and operational effectiveness.
Delving Deeper into the Advantages of Cloud Computing
Cloud computing significantly impacts healthcare by providing:
- Cost Reduction: Transitioning to the cloud minimizes the need for extensive on-site IT infrastructure, decreasing capital expenditure and maintenance costs.
- Enhanced Collaboration: The cloud facilitates seamless data sharing and communication among healthcare professionals, leading to better patient outcomes.
- Improved Data Management: Cloud solutions provide robust data storage and management capabilities, ensuring data is secure, accessible, and compliant with healthcare regulations.
- Scalability and Flexibility: Healthcare organizations can quickly scale their cloud resources to meet changing demands without investing in additional hardware.
- Business Continuity: Cloud-based backup and disaster recovery solutions ensure that critical data and applications are always available, even in the event of a disaster.
According to research from Stanford University’s Department of Computer Science, cloud computing reduces IT costs for healthcare providers by up to 30% while improving data accessibility and security. Embrace the future of healthcare with pioneer-technology.com and discover how cloud solutions can transform your organization.
3. What Are the Main Security Challenges in Healthcare Cloud Computing?
Healthcare cloud computing faces significant security challenges, including data breaches, privacy violations, and compliance issues. Maintaining patient confidentiality, ensuring data integrity, and protecting against cyber threats are critical concerns that healthcare organizations must address.
Further Examination of Security Challenges
Specific security challenges in healthcare cloud computing include:
- Data Breaches: Unauthorized access to sensitive patient information.
- Privacy Violations: Non-compliance with regulations like HIPAA.
- Compliance Issues: Difficulties in meeting stringent healthcare compliance standards.
- Insider Threats: Risks posed by employees or insiders with access to data.
- Cyber Threats: Vulnerabilities to malware, ransomware, and phishing attacks.
- Data Integrity: Ensuring data accuracy and reliability.
- Access Control: Managing and controlling access to patient data.
Addressing these challenges requires a multi-faceted approach that includes robust security measures, compliance protocols, and ongoing risk assessment.
4. How Can Healthcare Organizations Ensure Data Security in the Cloud?
Healthcare organizations can ensure data security in the cloud by implementing strong encryption, access controls, and regular security audits. Compliance with regulations like HIPAA and HITRUST is essential, as is continuous monitoring and employee training on security best practices.
Elaborating on Data Security Measures
To bolster data security in the cloud, healthcare organizations should:
- Implement Encryption: Encrypt data at rest and in transit to protect it from unauthorized access.
- Enforce Access Controls: Use role-based access controls (RBAC) to limit data access to authorized personnel.
- Conduct Regular Security Audits: Perform routine audits to identify vulnerabilities and ensure compliance.
- Comply with Regulations: Adhere to HIPAA, HITRUST, and other relevant standards.
- Monitor Continuously: Employ real-time monitoring tools to detect and respond to security incidents.
- Provide Employee Training: Train staff on security best practices and compliance requirements.
- Use Multi-Factor Authentication (MFA): Add an extra layer of security by requiring multiple verification methods.
- Implement Data Loss Prevention (DLP): Use DLP tools to prevent sensitive data from leaving the organization.
By implementing these measures, healthcare organizations can significantly enhance their data security posture in the cloud.
5. What Role Does Data Encryption Play in Securing Healthcare Data in the Cloud?
Data encryption is crucial for securing healthcare data in the cloud by converting sensitive information into an unreadable format, protecting it from unauthorized access. Encryption ensures that even if data is intercepted, it remains unintelligible without the decryption key, safeguarding patient privacy and data integrity.
Deep Dive into Data Encryption
Key aspects of data encryption in healthcare include:
- Protection Against Unauthorized Access: Encryption renders data unreadable to unauthorized users, safeguarding patient privacy.
- Data Integrity: Encryption ensures that data remains unaltered during storage and transmission.
- Compliance with Regulations: Many healthcare regulations, such as HIPAA, mandate encryption to protect patient data.
- Types of Encryption: Symmetric-key encryption (e.g., AES) and asymmetric-key encryption (e.g., RSA) offer different security levels and performance characteristics.
- Encryption Best Practices: Using strong encryption algorithms, managing encryption keys securely, and regularly updating encryption protocols are essential.
According to a report by the U.S. Department of Health and Human Services, data encryption is a critical component of a comprehensive security strategy for protecting electronic protected health information (ePHI). At pioneer-technology.com, we explore the latest encryption technologies and best practices for securing healthcare data.
6. What Are the Best Practices for Access Control in Healthcare Cloud Environments?
Best practices for access control in healthcare cloud environments include implementing role-based access control (RBAC), using multi-factor authentication (MFA), and regularly reviewing access privileges. These measures ensure that only authorized personnel can access sensitive patient data, reducing the risk of data breaches and privacy violations.
Expanding on Access Control Best Practices
Specific access control best practices include:
- Role-Based Access Control (RBAC): Assigning access permissions based on job roles ensures that users only have access to the data they need.
- Multi-Factor Authentication (MFA): Requiring multiple verification methods adds an extra layer of security, making it harder for unauthorized users to gain access.
- Regular Access Reviews: Periodically reviewing and updating access privileges ensures that users no longer have access to data they don’t need.
- Principle of Least Privilege: Granting users the minimum level of access required to perform their job functions.
- Audit Trails: Maintaining detailed logs of all access attempts and data modifications for auditing and monitoring purposes.
- Strong Password Policies: Enforcing strong password requirements and encouraging regular password updates.
- Conditional Access: Implementing policies that grant access based on specific conditions, such as location, device, or user behavior.
By implementing these best practices, healthcare organizations can strengthen their access control measures and protect sensitive patient data in the cloud.
7. How Does HIPAA Compliance Impact Cloud Security in Healthcare?
HIPAA compliance significantly impacts cloud security in healthcare by mandating strict standards for protecting patient data. Healthcare organizations must ensure their cloud providers meet HIPAA requirements, including implementing administrative, physical, and technical safeguards to protect the confidentiality, integrity, and availability of protected health information (PHI).
Detailed Look at HIPAA Compliance
Key aspects of HIPAA compliance in the cloud include:
- Business Associate Agreements (BAAs): Healthcare organizations must have BAAs with their cloud providers, outlining the provider’s responsibilities for protecting PHI.
- Administrative Safeguards: Implementing policies and procedures to manage and protect PHI, including risk assessments, security training, and incident response plans.
- Physical Safeguards: Implementing physical controls to protect data centers and other physical assets, such as access controls and surveillance systems.
- Technical Safeguards: Implementing technical measures to protect PHI, such as encryption, access controls, and audit trails.
- Regular Audits: Conducting regular audits to ensure compliance with HIPAA standards and identify potential vulnerabilities.
- Data Breach Notification: Complying with HIPAA’s data breach notification rule, which requires organizations to notify affected individuals and the Department of Health and Human Services (HHS) in the event of a breach.
According to the HHS, failure to comply with HIPAA can result in significant fines and penalties.
8. What Are the Key Considerations When Choosing a Cloud Provider for Healthcare Data?
When choosing a cloud provider for healthcare data, key considerations include security certifications, HIPAA compliance, data residency, and service level agreements (SLAs). Organizations should also assess the provider’s data governance policies, incident response capabilities, and ability to support their specific needs and regulatory requirements.
Expanding on Choosing a Cloud Provider
Specific considerations include:
- Security Certifications: Look for providers with certifications such as ISO 27001, SOC 2, and HITRUST CSF, which demonstrate a commitment to security.
- HIPAA Compliance: Ensure the provider can sign a BAA and meets all HIPAA requirements.
- Data Residency: Understand where the provider stores data and ensure it complies with data residency requirements.
- Service Level Agreements (SLAs): Review the SLAs to ensure they meet your availability, performance, and support needs.
- Data Governance Policies: Assess the provider’s policies for data retention, access, and disposal.
- Incident Response Capabilities: Evaluate the provider’s ability to detect, respond to, and recover from security incidents.
- Scalability and Flexibility: Ensure the provider can scale its services to meet your changing needs.
- Cost: Consider the total cost of ownership, including storage, compute, and network costs.
- References and Reviews: Check references and read reviews from other healthcare organizations to assess the provider’s reputation.
By carefully evaluating these factors, healthcare organizations can choose a cloud provider that meets their security, compliance, and business needs.
9. How Can Regular Security Audits Improve Healthcare Cloud Security?
Regular security audits improve healthcare cloud security by identifying vulnerabilities, ensuring compliance, and validating security controls. Audits help organizations proactively address risks, maintain data integrity, and protect patient privacy, enhancing overall security posture and reducing the likelihood of data breaches.
Elaborating on Security Audits
Benefits of regular security audits include:
- Vulnerability Identification: Audits uncover security weaknesses and vulnerabilities that could be exploited by attackers.
- Compliance Validation: Audits ensure compliance with HIPAA, HITRUST, and other regulatory requirements.
- Control Validation: Audits verify that security controls are functioning as intended and providing adequate protection.
- Risk Assessment: Audits help organizations assess and prioritize risks based on their potential impact.
- Continuous Improvement: Audits provide insights for continuous improvement of security policies and procedures.
- Stakeholder Confidence: Audits demonstrate a commitment to security, building trust with patients, partners, and regulators.
- Best Practices: Audits help organizations align with industry best practices and standards.
According to a study by the Ponemon Institute, organizations that conduct regular security audits experience fewer data breaches and lower breach costs.
10. What Emerging Technologies Enhance Cloud Security in Healthcare?
Emerging technologies enhancing cloud security in healthcare include AI-driven threat detection, blockchain for data integrity, and homomorphic encryption for secure data processing. These innovations offer advanced capabilities to protect patient data, improve security monitoring, and enable secure data sharing, strengthening the overall security posture of healthcare cloud environments.
Detailed Look at Emerging Technologies
Specific technologies include:
- AI-Driven Threat Detection: AI and machine learning algorithms can analyze large volumes of data to detect and respond to security threats in real-time.
- Blockchain for Data Integrity: Blockchain technology can ensure the integrity and immutability of healthcare data, providing a secure and transparent record of transactions.
- Homomorphic Encryption: Homomorphic encryption allows data to be processed in the cloud without being decrypted, protecting its confidentiality.
- Secure Multi-Party Computation (SMPC): SMPC enables multiple parties to jointly compute a function over their data without revealing their individual inputs.
- Zero-Trust Architecture: Zero-trust architecture assumes that no user or device is trusted by default and requires strict authentication and authorization for every access request.
- Confidential Computing: Confidential computing technologies protect data in use by creating a secure enclave where sensitive data can be processed.
By leveraging these emerging technologies, healthcare organizations can enhance their cloud security capabilities and stay ahead of evolving threats.
Explore more insights and solutions for securing your healthcare data in the cloud at pioneer-technology.com.
 Cloud-based Healthcare Solutions
Cloud-based Healthcare Solutions
11. What Are The Key Steps for Migrating Healthcare Data To The Cloud Securely?
Key steps include assessing data sensitivity, choosing a HIPAA-compliant cloud provider, encrypting data in transit and at rest, implementing strong access controls, and conducting thorough security testing. A well-planned migration ensures data remains protected throughout the process, maintaining compliance and minimizing risks.
Comprehensive Strategy for Secure Data Migration
The process involves:
- Data Sensitivity Assessment: Identifying and classifying sensitive data to determine appropriate security measures.
- Choosing a Compliant Provider: Selecting a cloud provider that meets HIPAA and other regulatory requirements.
- Data Encryption: Encrypting data before, during, and after migration to protect it from unauthorized access.
- Access Controls Implementation: Setting up role-based access controls to limit data access to authorized personnel.
- Security Testing: Conducting penetration testing and vulnerability assessments to identify and address security weaknesses.
- Backup and Recovery Planning: Creating a plan for backing up and recovering data in case of a disaster.
- Employee Training: Training staff on security best practices and compliance requirements.
- Monitoring and Logging: Implementing tools to monitor data access and log security events.
- Incident Response Planning: Developing a plan for responding to security incidents and data breaches.
By following these steps, healthcare organizations can migrate their data to the cloud securely and maintain compliance with regulatory requirements.
12. How Can Healthcare Providers Benefit from Data Analytics in the Cloud While Maintaining Security?
Healthcare providers can leverage data analytics in the cloud for insights that improve patient care and operational efficiency. Maintaining security involves using anonymized or de-identified data, implementing strict access controls, and employing secure analytics platforms. These measures ensure that sensitive patient information remains protected while valuable insights are gained.
Deep Dive into Secure Data Analytics
Specific strategies include:
- Anonymization and De-identification: Removing or masking identifying information from patient data before analysis.
- Secure Analytics Platforms: Using cloud-based analytics platforms with built-in security features, such as encryption and access controls.
- Access Controls: Limiting access to analytics tools and data to authorized personnel.
- Data Governance Policies: Implementing policies for data retention, access, and disposal.
- Regular Security Audits: Conducting routine audits to ensure compliance with security and privacy standards.
- Privacy-Enhancing Technologies (PETs): Using technologies such as differential privacy and federated learning to protect patient data during analysis.
- Training and Awareness: Educating staff on the importance of data privacy and security in analytics.
By adopting these strategies, healthcare providers can harness the power of data analytics in the cloud while safeguarding patient data.
13. What Is A Business Associate Agreement (BAA), and Why Is It Important for Healthcare Cloud Security?
A Business Associate Agreement (BAA) is a contract between a healthcare provider and a cloud service provider that handles protected health information (PHI). It outlines the provider’s responsibilities for safeguarding PHI, ensuring compliance with HIPAA regulations. A BAA is critical for establishing clear expectations and legal obligations, protecting patient data and minimizing liability.
Essential Components of a BAA
The agreement should include:
- Definition of PHI: Clearly defining what constitutes protected health information.
- Permitted Uses and Disclosures: Specifying how the cloud provider can use and disclose PHI.
- HIPAA Compliance Requirements: Outlining the provider’s obligations to comply with HIPAA regulations.
- Security Obligations: Detailing the provider’s security measures to protect PHI.
- Breach Notification Requirements: Describing the provider’s responsibilities in the event of a data breach.
- Data Access and Return: Ensuring the provider can return or destroy PHI at the termination of the agreement.
- Indemnification: Specifying liability and indemnification in case of a breach or violation.
According to HIPAA regulations, healthcare providers must have a BAA in place with any cloud provider that handles PHI. Pioneer-technology.com offers resources and insights to help you navigate these requirements.
14. How Do Mobile Devices Impact Cloud Security in Healthcare, and What Can Be Done to Mitigate Risks?
Mobile devices can introduce security risks to healthcare cloud environments due to their portability and potential for loss or theft. Implementing strong mobile device management (MDM) policies, requiring encryption, using multi-factor authentication, and regularly updating security software are crucial for mitigating these risks and protecting patient data.
Effective Strategies for Mobile Device Security
To enhance security, healthcare organizations should:
- Mobile Device Management (MDM): Implementing MDM solutions to manage and secure mobile devices.
- Encryption: Requiring encryption of data stored on mobile devices.
- Multi-Factor Authentication (MFA): Using MFA to verify the identity of users accessing data on mobile devices.
- Remote Wipe Capability: Ensuring the ability to remotely wipe data from lost or stolen devices.
- Strong Password Policies: Enforcing strong password requirements for mobile devices.
- Application Security: Implementing security measures for mobile applications, such as code reviews and vulnerability assessments.
- Regular Security Updates: Keeping security software and operating systems up to date on mobile devices.
- Employee Training: Educating staff on mobile security best practices.
By implementing these strategies, healthcare organizations can minimize the risks associated with mobile devices and protect patient data in the cloud.
15. What Are The Potential Legal Consequences of A Data Breach in Healthcare Cloud Computing?
Data breaches in healthcare cloud computing can lead to significant legal consequences, including fines, penalties, lawsuits, and reputational damage. Non-compliance with HIPAA regulations can result in severe financial penalties, while affected individuals may file lawsuits seeking compensation for damages. A proactive approach to security and compliance is essential for minimizing these risks.
The Impact of Data Breaches
The potential consequences include:
- HIPAA Fines and Penalties: Civil and criminal penalties for non-compliance with HIPAA regulations.
- Lawsuits: Legal action by affected individuals seeking compensation for damages such as identity theft and emotional distress.
- Reputational Damage: Loss of trust and credibility among patients and stakeholders.
- Regulatory Investigations: Scrutiny from regulatory agencies such as the Department of Health and Human Services (HHS).
- Business Disruption: Costs associated with incident response, remediation, and legal proceedings.
- Contractual Liabilities: Potential breach of contract claims from business associates and other partners.
According to the HHS, HIPAA violations can result in fines ranging from $100 to $50,000 per violation, with a maximum penalty of $1.5 million per year. Pioneer-technology.com provides insights and resources to help healthcare organizations avoid these costly consequences.
16. How Can Cloud-Based Telemedicine Solutions Ensure Patient Data Security and Privacy?
Cloud-based telemedicine solutions can ensure patient data security and privacy by implementing end-to-end encryption, secure authentication protocols, and adherence to HIPAA regulations. Ensuring that data is protected during transmission and storage is critical for maintaining patient trust and complying with legal requirements.
Detailed Look at Telemedicine Security
Strategies include:
- End-to-End Encryption: Encrypting data from the patient’s device to the provider’s system to prevent unauthorized access.
- Secure Authentication: Using multi-factor authentication and other secure methods to verify the identity of users.
- HIPAA Compliance: Complying with HIPAA regulations for the protection of protected health information (PHI).
- Data Residency: Ensuring that data is stored in compliance with data residency requirements.
- Access Controls: Limiting access to patient data to authorized personnel.
- Audit Trails: Maintaining detailed logs of all access attempts and data modifications.
- Regular Security Assessments: Conducting routine assessments to identify and address security vulnerabilities.
By implementing these measures, cloud-based telemedicine solutions can provide secure and private healthcare services.
17. What Role Do Virtual Private Clouds (VPCs) Play in Healthcare Cloud Security?
Virtual Private Clouds (VPCs) play a crucial role in healthcare cloud security by providing isolated network environments for sensitive data and applications. VPCs enable organizations to control network access, implement custom security policies, and protect data from unauthorized access, enhancing overall security posture.
Benefits of VPCs in Healthcare
Key advantages include:
- Network Isolation: VPCs provide isolated network environments that prevent unauthorized access to sensitive data.
- Custom Security Policies: Organizations can implement custom security policies to meet their specific needs.
- Access Control: VPCs enable fine-grained control over network access, limiting access to authorized personnel.
- Compliance: VPCs help organizations comply with HIPAA and other regulatory requirements.
- Enhanced Security: VPCs reduce the risk of data breaches by isolating sensitive data and applications.
- Scalability: VPCs can be easily scaled to meet changing needs.
- Cost Savings: VPCs can reduce costs by optimizing resource utilization.
By leveraging VPCs, healthcare organizations can create secure and compliant cloud environments.
18. How Can Healthcare Organizations Effectively Manage And Monitor Third-Party Access To Cloud-Based Data?
Effective management and monitoring of third-party access involve implementing strict access controls, conducting regular security audits, and using continuous monitoring tools. Establishing clear agreements with third parties, requiring multi-factor authentication, and regularly reviewing access privileges are also essential for protecting sensitive patient data.
Best Practices for Third-Party Access Management
Strategies include:
- Access Controls: Implementing role-based access controls and the principle of least privilege.
- Security Audits: Conducting regular audits to ensure compliance with security policies and agreements.
- Continuous Monitoring: Using monitoring tools to detect and respond to unauthorized access attempts.
- Third-Party Agreements: Establishing clear agreements that outline security requirements and responsibilities.
- Multi-Factor Authentication (MFA): Requiring MFA for all third-party users.
- Access Reviews: Regularly reviewing and updating access privileges.
- Data Loss Prevention (DLP): Using DLP tools to prevent sensitive data from leaving the organization.
- Incident Response Planning: Developing a plan for responding to security incidents involving third parties.
By following these best practices, healthcare organizations can effectively manage and monitor third-party access to cloud-based data and protect patient information.
19. What Are The Best Practices For Data Backup And Disaster Recovery In Healthcare Cloud Environments?
Best practices for data backup and disaster recovery in healthcare cloud environments include regular automated backups, offsite data storage, and comprehensive disaster recovery plans. Regularly testing recovery procedures, using encryption, and ensuring compliance with HIPAA regulations are also crucial for maintaining data availability and protecting patient information.
Detailed Backup and Recovery Strategies
Key elements include:
- Regular Automated Backups: Implementing automated backups to ensure that data is regularly backed up.
- Offsite Data Storage: Storing backups in a separate location to protect against disasters.
- Disaster Recovery Plans: Creating comprehensive plans for recovering data and systems in the event of a disaster.
- Regular Testing: Regularly testing recovery procedures to ensure they are effective.
- Encryption: Encrypting backups to protect data from unauthorized access.
- HIPAA Compliance: Ensuring that backup and recovery procedures comply with HIPAA regulations.
- Redundancy: Implementing redundant systems to ensure high availability.
- Monitoring: Monitoring backup and recovery processes to ensure they are functioning properly.
By following these best practices, healthcare organizations can maintain data availability and protect patient information in the cloud.
20. How Can Pioneer-Technology.Com Help Healthcare Organizations Improve Cloud Security?
Pioneer-technology.com provides comprehensive insights, analysis, and resources to help healthcare organizations navigate the complexities of cloud security. Our expertise in emerging technologies, security best practices, and regulatory compliance empowers organizations to implement robust security measures and protect patient data in the cloud.
Benefits of Choosing Pioneer-Technology.Com
We offer:
- Expert Insights: Access to the latest trends and best practices in cloud security.
- Detailed Analysis: In-depth analysis of security challenges and solutions for healthcare cloud environments.
- Regulatory Compliance Guidance: Support for complying with HIPAA, HITRUST, and other regulatory requirements.
- Emerging Technology Expertise: Expertise in AI-driven threat detection, blockchain, and other emerging technologies.
- Customized Solutions: Tailored solutions to meet the specific needs of healthcare organizations.
- Training and Awareness Programs: Educational resources to help staff understand and implement security best practices.
- Community Support: Access to a community of experts and peers for sharing knowledge and best practices.
Visit pioneer-technology.com to explore our resources and discover how we can help you improve cloud security in your healthcare organization. Contact us at 450 Serra Mall, Stanford, CA 94305, United States, or call +1 (650) 723-2300.
Don’t wait to secure your healthcare data in the cloud. Visit pioneer-technology.com today and discover the latest insights and solutions.
FAQ Section on Cloud Technology in Healthcare
-
What is cloud computing in healthcare?
Cloud computing in healthcare is the practice of storing, managing, and processing healthcare-related data and applications on a network of remote servers rather than on local, on-site servers. This enables healthcare organizations to access resources and services over the internet, improving efficiency, scalability, and cost-effectiveness.
-
Why is cloud security important for healthcare organizations?
Cloud security is vital for healthcare organizations because it protects sensitive patient data from unauthorized access, breaches, and cyber threats. Ensuring data confidentiality, integrity, and availability is essential for maintaining patient trust, complying with regulations like HIPAA, and avoiding costly legal consequences.
-
How does HIPAA impact the use of cloud services in healthcare?
HIPAA (Health Insurance Portability and Accountability Act) sets strict standards for protecting patient data. Healthcare organizations must ensure their cloud providers meet HIPAA requirements, including implementing administrative, physical, and technical safeguards to protect the confidentiality, integrity, and availability of protected health information (PHI). Business Associate Agreements (BAAs) are essential contracts that outline these responsibilities.
-
What are the main benefits of using cloud technology in healthcare?
The primary benefits of using cloud technology in healthcare include increased efficiency, cost savings, improved data accessibility, enhanced collaboration, scalability, and disaster recovery. Cloud solutions streamline workflows, reduce IT infrastructure costs, and enable healthcare providers to access patient information from anywhere, improving patient care and operational effectiveness.
-
What are some of the key security challenges in healthcare cloud computing?
Key security challenges in healthcare cloud computing include data breaches, privacy violations, compliance issues, insider threats, cyber threats (such as malware and ransomware), data integrity, and access control. Addressing these challenges requires a multi-faceted approach that includes robust security measures, compliance protocols, and ongoing risk assessment.
-
What is a Business Associate Agreement (BAA), and why is it necessary?
A Business Associate Agreement (BAA) is a contract between a healthcare provider (covered entity) and a cloud service provider (business associate) that handles protected health information (PHI). It outlines the provider’s responsibilities for safeguarding PHI and ensuring compliance with HIPAA regulations. A BAA is necessary to establish clear expectations, legal obligations, and protect patient data.
-
How can healthcare organizations ensure data encryption in the cloud?
Healthcare organizations can ensure data encryption in the cloud by implementing strong encryption algorithms for data at rest and in transit. Using encryption key management best practices, regularly updating encryption protocols, and verifying that the cloud provider supports robust encryption methods are essential steps.
-
What is role-based access control (RBAC), and how does it improve security?
Role-based access control (RBAC) is a security mechanism that assigns access permissions based on an individual’s job role within the organization. By limiting data access to only authorized personnel who need it to perform their job functions, RBAC minimizes the risk of unauthorized access, data breaches, and insider threats.
-
What is multi-factor authentication (MFA), and why is it important in cloud security?
Multi-factor authentication (MFA) is a security process that requires users to provide multiple verification factors to gain access to a system or application. Using MFA adds an extra layer of security, making it more difficult for unauthorized users to gain access, even if they have a valid username and password.
-
How can pioneer-technology.com help healthcare organizations with cloud security?
pioneer-technology.com provides comprehensive insights, analysis, and resources to help healthcare organizations navigate the complexities of cloud security. We offer expertise in emerging technologies, security best practices, and regulatory compliance, empowering organizations to implement robust security measures, protect patient data in the cloud, and comply with HIPAA and other regulations.