Encryption Technology is the cornerstone of modern data security, transforming readable information into an unreadable format to protect its confidentiality. Pioneer-technology.com is dedicated to providing you with the latest insights into this crucial technology. By leveraging encryption techniques, we can safeguard sensitive data, ensure secure communications, and maintain data integrity, fostering a safer digital environment for everyone. Explore how encryption methods ensure data protection, secure communication, and overall data security.
1. Understanding Encryption Technology
Is encryption technology just about scrambling data?
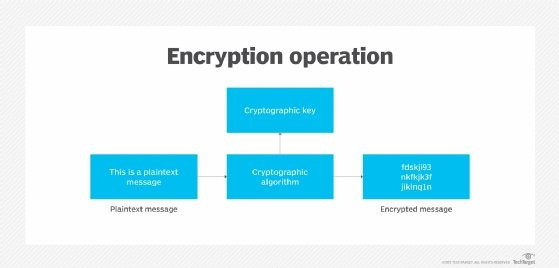
Encryption technology is a method of transforming data into an unreadable format, known as ciphertext, to protect its confidentiality and integrity. According to research from Stanford University’s Department of Computer Science, encryption methods are increasingly vital for securing data in transit and at rest. This process uses algorithms and keys to encode and decode information, ensuring only authorized parties can access the original data. Think of it as a digital lock and key, where the key is needed to unlock and read the message.
1.1. The Basics of Encryption
Encryption involves converting plaintext (readable data) into ciphertext (unreadable data) using an algorithm and a key. The algorithm is the mathematical formula used to scramble the data, while the key is a secret piece of information that unlocks the encryption. This ensures that even if the data is intercepted, it remains unintelligible to unauthorized users.
- Plaintext: Original, readable data.
- Ciphertext: Encrypted, unreadable data.
- Algorithm: Mathematical formula used for encryption.
- Key: Secret information needed to decrypt the data.
1.2. Types of Encryption Algorithms
What are the different types of encryption algorithms?
There are two primary types of encryption algorithms: symmetric and asymmetric. Symmetric encryption uses the same key for both encryption and decryption, making it faster but requiring secure key exchange. Asymmetric encryption, also known as public-key encryption, uses a pair of keys: a public key for encryption and a private key for decryption. This method is more secure but slower.
| Type | Key Usage | Speed | Security Level | Use Cases |
|---|---|---|---|---|
| Symmetric Encryption | Single key for both operations | Faster | High | Securing data at rest, encrypting large volumes of data |
| Asymmetric Encryption | Public and private key pair | Slower | Very High | Secure key exchange, digital signatures, encrypting small amounts of data |
1.3. Common Encryption Methods
What are some common encryption methods used today?
Several encryption methods are widely used today, each offering different levels of security and efficiency. Some of the most common include:
- Advanced Encryption Standard (AES): A symmetric encryption algorithm widely used for securing data at rest and in transit.
- RSA (Rivest-Shamir-Adleman): An asymmetric encryption algorithm used for secure key exchange and digital signatures.
- Triple DES (3DES): An older symmetric encryption algorithm, now largely replaced by AES due to its slower speed and lower security.
- Twofish: A symmetric key block cipher that supports key sizes up to 256 bits.
- Blowfish: A symmetric key block cipher that supports key sizes up to 448 bits.
1.4. The Role of Encryption Keys
How important are encryption keys in securing data?
Encryption keys are crucial for securing data, as they are the secret information needed to decrypt the ciphertext back into plaintext. The strength of the encryption depends heavily on the key length and the algorithm used to generate it. Longer keys provide higher security, as they are more difficult to crack through brute-force attacks. Proper key management is essential to maintain the security of encrypted data.
Address: 450 Serra Mall, Stanford, CA 94305, United States. Phone: +1 (650) 723-2300. Website: pioneer-technology.com.
 Symmetric encryption key
Symmetric encryption key
1.5. Real-World Applications of Encryption
Where is encryption technology used in our daily lives?
Encryption technology is used in numerous applications to protect sensitive data in our daily lives. These include:
- Secure Communication: Encrypting emails, messaging apps, and voice calls to ensure privacy.
- Online Transactions: Protecting financial data during online shopping and banking.
- Data Storage: Securing data stored on computers, servers, and cloud storage.
- Virtual Private Networks (VPNs): Encrypting internet traffic to protect online activity from eavesdropping.
- Wireless Security: Securing Wi-Fi networks with protocols like WPA3.
2. Why Encryption Technology Is Important
Why is encryption technology crucial for data protection?
Encryption technology is essential because it provides confidentiality, integrity, authentication, and non-repudiation for digital data. Encryption ensures that sensitive information remains protected from unauthorized access, thereby maintaining trust and security in various digital interactions. It is the foundation upon which modern data security is built.
2.1. Ensuring Data Confidentiality
How does encryption protect the confidentiality of data?
Encryption ensures data confidentiality by encoding it in a way that makes it unreadable to anyone without the correct decryption key. This is particularly important for protecting sensitive information such as personal data, financial records, and trade secrets. By encrypting data, organizations can prevent unauthorized access and disclosure, even in the event of a data breach.
- Protects sensitive information from unauthorized access.
- Maintains privacy of personal and financial data.
- Prevents disclosure of trade secrets and confidential business information.
2.2. Maintaining Data Integrity
Can encryption help ensure the integrity of data?
Yes, encryption helps maintain data integrity by ensuring that data is not altered or corrupted during storage or transmission. Encryption algorithms often include mechanisms to detect tampering, such as hash functions and digital signatures. If the data is modified, the decryption process will fail, or the digital signature will be invalid, alerting the recipient to the alteration.
2.3. Facilitating Secure Communication
How does encryption enable secure communication channels?
Encryption facilitates secure communication by creating a protected channel for transmitting data between parties. Protocols like Transport Layer Security (TLS) and Secure Sockets Layer (SSL) use encryption to secure internet traffic, ensuring that data exchanged between web browsers and servers remains private and protected from eavesdropping. This is crucial for secure online transactions, email communication, and other forms of digital communication.
2.4. Supporting Authentication and Non-Repudiation
What role does encryption play in authentication and non-repudiation?
Encryption supports authentication by verifying the identity of the sender and ensuring that the data has not been tampered with. Digital signatures, which use asymmetric encryption, allow the recipient to verify that the message came from the claimed sender and that the content has not been altered. Non-repudiation ensures that the sender cannot deny having sent the message, providing a secure and reliable means of communication.
| Function | Description | Encryption Method |
|---|---|---|
| Authentication | Verifies the identity of the sender and ensures data integrity. | Digital Signatures |
| Non-Repudiation | Ensures the sender cannot deny sending the message, providing reliable communication. | Asymmetric Keys |
2.5. Meeting Compliance and Regulatory Requirements
Why is encryption often required by compliance regulations?
Many compliance regulations, such as the Payment Card Industry Data Security Standard (PCI DSS), the Health Insurance Portability and Accountability Act (HIPAA), and the General Data Protection Regulation (GDPR), require organizations to encrypt sensitive data to protect it from unauthorized access and disclosure. Encryption helps organizations meet these regulatory requirements and avoid costly penalties and legal liabilities.
According to the Payment Card Industry Data Security Standard, merchants are required to encrypt customer payment card data both when it is stored and when it is transmitted across public networks.
3. How Encryption Technology Works
What are the underlying mechanisms of encryption technology?
Encryption technology works through a combination of algorithms, keys, and protocols to transform plaintext into ciphertext and vice versa. The process involves several steps, including key generation, encryption, transmission, and decryption. Understanding these mechanisms is crucial for appreciating the security and complexity of encryption technology.
3.1. The Encryption Process: From Plaintext to Ciphertext
How is plaintext transformed into ciphertext using encryption?
The encryption process begins with the plaintext, which is the original, readable data. The encryption algorithm takes this plaintext and, using a secret key, transforms it into ciphertext. This transformation involves mathematical operations such as substitution, transposition, and modular arithmetic. The result is an unreadable, scrambled version of the original data.
- Input: Plaintext data.
- Process: Encryption algorithm applies the key.
- Output: Ciphertext data.
3.2. Key Generation and Management
How are encryption keys generated and managed securely?
Key generation involves creating a random string of bits that serves as the secret key for encryption. The strength of the encryption depends on the randomness and length of the key. Secure key management practices are essential to protect keys from unauthorized access, theft, or loss. This includes storing keys in secure locations, limiting access to authorized personnel, and using key management systems.
3.3. Symmetric vs. Asymmetric Encryption in Detail
What are the key differences between symmetric and asymmetric encryption?
Symmetric encryption uses the same key for both encryption and decryption, making it faster and more efficient for encrypting large amounts of data. However, it requires a secure method for exchanging the key between parties. Asymmetric encryption, on the other hand, uses a pair of keys: a public key for encryption and a private key for decryption. The public key can be shared with anyone, while the private key must be kept secret. Asymmetric encryption is more secure but slower, making it suitable for secure key exchange and digital signatures.
| Feature | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Key Usage | Single key for both encryption and decryption | Public key for encryption, private key for decryption |
| Speed | Faster | Slower |
| Security Level | Requires secure key exchange | More secure, no need for secure key exchange |
| Use Cases | Encrypting large volumes of data, data at rest | Secure key exchange, digital signatures |
3.4. Cryptographic Protocols: TLS/SSL, SSH, and More
What are some common cryptographic protocols and how do they use encryption?
Cryptographic protocols are sets of rules and standards that define how encryption is used to secure communication channels. Some of the most common protocols include:
- Transport Layer Security (TLS)/Secure Sockets Layer (SSL): Used to secure internet traffic between web browsers and servers.
- Secure Shell (SSH): Used to secure remote access to servers and network devices.
- Internet Protocol Security (IPsec): Used to secure network communications at the IP layer.
- Secure Multipurpose Internet Mail Extensions (S/MIME): Used to secure email communication.
3.5. Decryption: Converting Ciphertext Back to Plaintext
How is ciphertext converted back into readable plaintext?
Decryption is the reverse process of encryption, where ciphertext is converted back into plaintext using the correct decryption key and algorithm. The decryption algorithm applies the key to the ciphertext, reversing the mathematical operations performed during encryption. If the key is correct, the original plaintext data is recovered.
4. Types of Encryption Technology
What are the different types of encryption technology available?
There are numerous types of encryption technology, each designed for specific use cases and security requirements. These include end-to-end encryption, full-disk encryption, homomorphic encryption, and more. Understanding these different types can help organizations choose the right encryption solutions for their needs.
4.1. End-to-End Encryption (E2EE)
What is end-to-end encryption and how does it protect communication?
End-to-end encryption (E2EE) is a method of securing communication in which only the sender and recipient can read the messages. The messages are encrypted on the sender’s device and decrypted on the recipient’s device, with no intermediary able to access the plaintext. This provides a high level of privacy and security, as even the service provider cannot read the messages. Messaging apps like WhatsApp and Signal use E2EE to protect user communications.
4.2. Full-Disk Encryption (FDE)
How does full-disk encryption protect data on storage devices?
Full-disk encryption (FDE) is a method of encrypting the entire contents of a storage device, such as a hard drive or solid-state drive. This protects all data on the device, including the operating system, applications, and user files. FDE ensures that if the device is lost or stolen, the data remains inaccessible to unauthorized users.
4.3. Homomorphic Encryption
What is homomorphic encryption and what are its potential applications?
Homomorphic encryption is a type of encryption that allows computations to be performed on ciphertext without decrypting it first. This means that data can be processed and analyzed without exposing the underlying plaintext. Homomorphic encryption has numerous potential applications, including secure cloud computing, privacy-preserving data analysis, and secure voting systems.
4.4. Column-Level Encryption
What is column-level encryption and how does it enhance database security?
Column-level encryption is a method of encrypting individual columns within a database table. This allows organizations to protect sensitive data fields, such as credit card numbers or social security numbers, while leaving other data fields unencrypted. Column-level encryption enhances database security by limiting the exposure of sensitive data in the event of a data breach.
4.5. Encryption as a Service (EaaS)
What is Encryption as a Service and what are its benefits?
Encryption as a Service (EaaS) is a cloud-based service that provides encryption capabilities to organizations. This allows organizations to encrypt their data without the need to manage their own encryption infrastructure. EaaS offers several benefits, including reduced costs, simplified management, and improved scalability.
5. Implementing Encryption Technology
What are the key steps in implementing encryption technology effectively?
Implementing encryption technology effectively requires careful planning, execution, and management. This includes assessing security needs, selecting the right encryption solutions, implementing encryption policies, and regularly monitoring and updating encryption systems. Proper implementation is essential for maximizing the security benefits of encryption technology.
5.1. Assessing Security Needs and Risks
How should organizations assess their security needs before implementing encryption?
Before implementing encryption, organizations should conduct a thorough assessment of their security needs and risks. This includes identifying sensitive data assets, evaluating potential threats, and determining the level of protection required. The assessment should also consider compliance and regulatory requirements, as well as business and operational needs.
5.2. Selecting the Right Encryption Solutions
How can organizations choose the best encryption solutions for their requirements?
Choosing the right encryption solutions involves considering various factors, including the type of data to be protected, the level of security required, the performance impact, and the cost. Organizations should evaluate different encryption algorithms, protocols, and solutions, and select those that best meet their specific needs and requirements.
- Identify sensitive data assets.
- Evaluate potential threats.
- Determine the level of protection required.
- Consider compliance requirements.
- Balance business and operational needs.
5.3. Developing Encryption Policies and Procedures
Why are encryption policies and procedures important for data protection?
Encryption policies and procedures are essential for ensuring that encryption is implemented and managed consistently across the organization. These policies should define the scope of encryption, the types of data to be encrypted, the encryption algorithms and keys to be used, and the procedures for key management and access control.
5.4. Key Management Best Practices
What are the best practices for managing encryption keys securely?
Secure key management is crucial for maintaining the security of encrypted data. Best practices for key management include:
- Generating strong, random keys.
- Storing keys in secure locations, such as hardware security modules (HSMs).
- Limiting access to authorized personnel.
- Implementing key rotation policies.
- Backing up keys securely.
- Auditing key usage.
5.5. Monitoring and Updating Encryption Systems
Why is it important to monitor and update encryption systems regularly?
Regular monitoring and updating of encryption systems are essential for maintaining their effectiveness and security. This includes monitoring for vulnerabilities, applying security patches, and updating encryption algorithms and protocols as needed. Regular monitoring and updating help ensure that encryption systems remain resilient against evolving threats.
6. Challenges and Limitations of Encryption Technology
What are the main challenges and limitations associated with encryption technology?
Despite its many benefits, encryption technology also has several challenges and limitations. These include key management complexities, performance overhead, legal and regulatory issues, and the potential for misuse. Understanding these challenges is crucial for addressing them effectively and maximizing the benefits of encryption technology.
6.1. Key Management Complexity
Why is key management one of the biggest challenges in using encryption?
Key management is one of the biggest challenges in using encryption because it involves securely generating, storing, distributing, and revoking encryption keys. Poor key management practices can compromise the security of encrypted data, making it vulnerable to unauthorized access. Organizations need to implement robust key management systems and policies to address this challenge.
According to research from pioneer-technology.com, managing encryption keys throughout their lifecycle and protecting them from theft, loss, or misuse requires strategies.
6.2. Performance Overhead
How does encryption affect system performance and what can be done to mitigate this?
Encryption can introduce performance overhead due to the computational resources required to encrypt and decrypt data. This can slow down system performance, particularly for large volumes of data or high-traffic applications. Mitigation strategies include using hardware acceleration, optimizing encryption algorithms, and implementing caching mechanisms.
6.3. Legal and Regulatory Issues
What are the legal and regulatory challenges associated with encryption?
Encryption can raise legal and regulatory issues, particularly in the context of law enforcement and national security. Governments may seek access to encrypted data for investigative purposes, leading to debates about privacy rights and the balance between security and liberty. Organizations need to be aware of these legal and regulatory challenges and ensure that their encryption practices comply with applicable laws and regulations.
6.4. Potential for Misuse
How can encryption technology be misused for malicious purposes?
Encryption technology can be misused for malicious purposes, such as hiding criminal activity, facilitating terrorism, and deploying ransomware attacks. Cybercriminals use encryption to protect their communications and data, making it difficult for law enforcement to track and prosecute them. Organizations need to be aware of this potential for misuse and take steps to prevent it.
6.5. Backdoors and Vulnerabilities
What are the risks associated with encryption backdoors and vulnerabilities?
Encryption backdoors are intentional weaknesses in encryption systems that allow authorized parties, such as law enforcement agencies, to bypass the encryption. While backdoors may be intended for legitimate purposes, they also create opportunities for злоумышленники to exploit the system. Vulnerabilities in encryption algorithms and implementations can also compromise the security of encrypted data, allowing злоумышленники to bypass the encryption.
7. The Future of Encryption Technology
What are the emerging trends and future directions in encryption technology?
The future of encryption technology is shaped by emerging trends such as quantum-resistant cryptography, homomorphic encryption, and decentralized encryption. These technologies promise to enhance the security, privacy, and versatility of encryption, enabling new applications and use cases.
7.1. Quantum-Resistant Cryptography
What is quantum-resistant cryptography and why is it important?
Quantum-resistant cryptography, also known as post-quantum cryptography, is a type of encryption that is designed to resist attacks from quantum computers. Quantum computers have the potential to break many of the currently used encryption algorithms, such as RSA and ECC. Quantum-resistant cryptography uses algorithms that are believed to be secure against both classical and quantum computers.
7.2. Homomorphic Encryption Advancements
How is homomorphic encryption evolving and what new applications are emerging?
Homomorphic encryption is evolving rapidly, with new algorithms and techniques being developed to improve its performance and versatility. Emerging applications of homomorphic encryption include secure cloud computing, privacy-preserving data analysis, secure voting systems, and secure machine learning.
7.3. Decentralized Encryption
What is decentralized encryption and how does it enhance privacy and security?
Decentralized encryption is a type of encryption that is based on decentralized technologies such as blockchain and distributed ledgers. This allows for more secure and private data storage and communication, as there is no central authority that can access or control the data. Decentralized encryption is being used in applications such as secure messaging, digital identity management, and decentralized finance.
7.4. Lightweight Cryptography
What is lightweight cryptography and why is it important for IoT devices?
Lightweight cryptography is a type of encryption that is designed to be efficient and low-power, making it suitable for use in resource-constrained devices such as IoT devices and mobile devices. Lightweight cryptography algorithms are optimized for performance and energy efficiency, while still providing adequate security.
7.5. AI and Encryption
How is artificial intelligence influencing the field of encryption technology?
Artificial intelligence (AI) is influencing the field of encryption technology in several ways. AI can be used to analyze encrypted data, identify vulnerabilities in encryption systems, and develop new encryption algorithms. AI can also be used to automate key management tasks and improve the efficiency of encryption processes.
8. Encryption and Cybersecurity
How does encryption contribute to overall cybersecurity strategies?
Encryption is a critical component of overall cybersecurity strategies, providing essential protection for data, systems, and networks. Encryption helps organizations mitigate the risks of data breaches, cyberattacks, and other security incidents.
8.1. Protecting Data at Rest
How does encryption secure data when it is stored on devices and servers?
Encryption protects data at rest by encoding it in a way that makes it unreadable to unauthorized users. This is particularly important for protecting sensitive data stored on devices such as laptops, smartphones, and USB drives, as well as on servers and cloud storage.
8.2. Securing Data in Transit
How does encryption ensure the security of data as it travels across networks?
Encryption secures data in transit by creating a protected channel for transmitting data between parties. Protocols like TLS/SSL and SSH use encryption to secure internet traffic and remote access sessions, ensuring that data exchanged between devices remains private and protected from eavesdropping.
8.3. Preventing Data Breaches
How can encryption help organizations prevent data breaches and mitigate their impact?
Encryption can help organizations prevent data breaches by making it more difficult for злоумышленники to access sensitive data. Even if a data breach occurs, encryption can mitigate the impact by rendering the stolen data unreadable to злоумышленники.
8.4. Complying with Data Protection Regulations
How does encryption support compliance with data protection regulations like GDPR and HIPAA?
Encryption supports compliance with data protection regulations such as GDPR and HIPAA by providing a means of protecting sensitive data from unauthorized access and disclosure. These regulations require organizations to implement appropriate security measures to protect personal data, and encryption is often a key component of these measures.
8.5. Enhancing Network Security
How does encryption contribute to the overall security of networks and systems?
Encryption enhances network security by providing a means of securing communication channels, authenticating users and devices, and protecting data from eavesdropping and tampering. Encryption is used in protocols such as VPNs and IPsec to create secure connections between networks and systems.
9. Common Encryption Algorithms
Which encryption algorithms are most widely used and trusted today?
Several encryption algorithms are widely used and trusted today, each offering different levels of security and efficiency. These include AES, RSA, ECC, and more. Understanding these algorithms is crucial for selecting the right encryption solutions for specific needs.
9.1. Advanced Encryption Standard (AES)
What makes AES the most widely used symmetric encryption algorithm?
Advanced Encryption Standard (AES) is the most widely used symmetric encryption algorithm due to its high security, efficiency, and versatility. AES is used to encrypt data in various applications, including data at rest, data in transit, and secure communication channels.
9.2. RSA (Rivest-Shamir-Adleman)
Why is RSA a popular choice for asymmetric encryption and digital signatures?
RSA (Rivest-Shamir-Adleman) is a popular choice for asymmetric encryption and digital signatures due to its strong security, wide availability, and well-established standards. RSA is used to secure key exchange, digital signatures, and secure communication channels.
9.3. Elliptic Curve Cryptography (ECC)
What are the advantages of ECC over traditional encryption algorithms?
Elliptic Curve Cryptography (ECC) offers several advantages over traditional encryption algorithms, including smaller key sizes, faster performance, and higher security. ECC is used in applications such as mobile devices, IoT devices, and secure communication channels.
9.4. Triple DES (3DES)
Why is Triple DES considered outdated but still used in some legacy systems?
Triple DES (3DES) is considered outdated but is still used in some legacy systems because it was widely adopted in the past and is supported by many older devices and applications. However, 3DES is slower and less secure than newer encryption algorithms such as AES.
9.5. Blowfish and Twofish
What are the key features and applications of Blowfish and Twofish algorithms?
Blowfish and Twofish are symmetric encryption algorithms that offer high security and performance. Blowfish is known for its simplicity and ease of implementation, while Twofish is known for its advanced features and resistance to cryptanalysis. These algorithms are used in various applications, including data storage, secure communication, and network security.
10. Encryption and the Future of Privacy
How will encryption shape the future of privacy in the digital age?
Encryption will play a crucial role in shaping the future of privacy in the digital age, providing individuals and organizations with the tools they need to protect their data and communications from unauthorized access. As technology evolves and new threats emerge, encryption will continue to be a vital component of privacy-enhancing technologies.
10.1. Encryption as a Fundamental Right
Why is access to strong encryption considered a fundamental right by privacy advocates?
Access to strong encryption is considered a fundamental right by privacy advocates because it enables individuals to protect their personal data, communicate privately, and exercise their freedom of expression. Encryption empowers individuals to control their own information and resist government surveillance and corporate data collection.
10.2. Balancing Security and Privacy
How can society strike a balance between the need for security and the right to privacy in the context of encryption?
Striking a balance between the need for security and the right to privacy in the context of encryption requires careful consideration of the trade-offs between these competing values. Society needs to develop policies and regulations that promote the responsible use of encryption, while also protecting the rights and freedoms of individuals.
10.3. The Role of Governments and Law Enforcement
What role should governments and law enforcement agencies play in regulating encryption technology?
Governments and law enforcement agencies have a legitimate interest in regulating encryption technology to prevent its misuse for criminal purposes. However, it is important to ensure that these regulations do not undermine the security and privacy of individuals and organizations. Governments should focus on promoting the responsible use of encryption, while also respecting the rights and freedoms of individuals.
10.4. Encryption and Digital Identity
How can encryption be used to enhance digital identity and protect personal information online?
Encryption can be used to enhance digital identity and protect personal information online by providing a secure means of authenticating users, verifying their credentials, and protecting their data from unauthorized access. Encryption is used in technologies such as digital certificates, secure tokens, and biometric authentication to enhance digital identity and protect personal information online.
10.5. Empowering Individuals with Privacy Tools
How can individuals be empowered with the knowledge and tools they need to protect their privacy using encryption?
Individuals can be empowered with the knowledge and tools they need to protect their privacy using encryption through education, awareness campaigns, and the development of user-friendly encryption tools. It is important to provide individuals with the information they need to understand the benefits of encryption and how to use it effectively.
Do you want to dive deeper into the world of encryption technology? Visit pioneer-technology.com for more in-depth articles, the latest technological breakthroughs, and expert analysis. Stay ahead of the curve and discover the full potential of encryption.
FAQ: Frequently Asked Questions About Encryption Technology
1. What is encryption?
Encryption is the process of converting readable data (plaintext) into an unreadable format (ciphertext) to protect its confidentiality and integrity.
2. Why is encryption important?
Encryption is crucial for protecting sensitive data from unauthorized access, ensuring secure communications, and meeting compliance and regulatory requirements.
3. What are the different types of encryption?
The primary types of encryption are symmetric (using the same key for encryption and decryption) and asymmetric (using a public-private key pair).
4. What is AES?
Advanced Encryption Standard (AES) is a widely used symmetric encryption algorithm known for its high security and efficiency.
5. What is RSA?
RSA (Rivest-Shamir-Adleman) is a popular asymmetric encryption algorithm used for secure key exchange and digital signatures.
6. What is end-to-end encryption (E2EE)?
E2EE ensures that only the sender and recipient can read the messages, with no intermediary able to access the plaintext.
7. What is full-disk encryption (FDE)?
FDE encrypts the entire contents of a storage device, protecting all data on the device from unauthorized access.
8. What is homomorphic encryption?
Homomorphic encryption allows computations to be performed on ciphertext without decrypting it first, ensuring data privacy during processing.
9. How does encryption contribute to cybersecurity?
Encryption helps prevent data breaches, secures data in transit and at rest, and enhances overall network security.
10. What are the challenges of encryption?
Key management complexity, performance overhead, legal and regulatory issues, and the potential for misuse are significant challenges associated with encryption.

