Spread spectrum technology is a signal transmission technique that spreads a signal over a wide frequency band, making it more resistant to interference and jamming. At pioneer-technology.com, we help you explore and understand the latest advancements in communication technology. Dive in to discover how this pivotal technology enhances security, reliability, and efficiency in wireless communications, and how it’s revolutionizing modern technology. Stay informed with our in-depth analysis and cutting-edge insights into signal processing and digital communication.
1. What Exactly Is Spread Spectrum Technology?
Spread spectrum technology is a method of transmitting radio signals by spreading them over a wide frequency band. This contrasts with narrow-band transmission, which concentrates the signal into a narrow frequency range. The primary goal of spread spectrum is to increase resistance to interference, jamming, and eavesdropping. By spreading the signal, the power spectral density is reduced, making it harder to detect and intercept.
1.1 How Does It Differ From Traditional Narrowband Transmission?
Traditional narrowband transmission concentrates the signal into a small frequency range, which makes it efficient in terms of bandwidth usage but also more vulnerable to interference. Spread spectrum, on the other hand, sacrifices bandwidth efficiency for increased robustness. Here’s a quick comparison:
| Feature | Narrowband Transmission | Spread Spectrum Transmission |
|---|---|---|
| Bandwidth Usage | Efficient, uses a narrow frequency range | Inefficient, uses a wide frequency range |
| Interference | Highly susceptible | Highly resistant |
| Security | Less secure | More secure |
| Complexity | Simpler implementation | More complex implementation |
| Power Density | Higher | Lower |
1.2 What Are the Key Advantages of Using Spread Spectrum?
Spread spectrum offers several key advantages, making it suitable for a wide range of applications. These include:
- Interference Resistance: The wideband nature of spread spectrum signals makes them less susceptible to narrowband interference.
- Jamming Resistance: It is difficult for jammers to disrupt the entire wideband signal.
- Security: The signal is spread over a wide band, making it harder to detect and intercept, thus enhancing security.
- Code Division Multiple Access (CDMA): Multiple users can share the same frequency band simultaneously by using different spreading codes.
- Multipath Mitigation: Spread spectrum techniques can mitigate the effects of multipath fading, which occurs when signals arrive at the receiver via multiple paths.
1.3 What Are the Different Types of Spread Spectrum Techniques?
There are several types of spread spectrum techniques, each with its own characteristics and applications. The most common types include:
- Direct Sequence Spread Spectrum (DSSS)
- Frequency Hopping Spread Spectrum (FHSS)
- Time Hopping Spread Spectrum (THSS)
- Chirp Spread Spectrum (CSS)
2. What is Direct Sequence Spread Spectrum (DSSS)?
Direct Sequence Spread Spectrum (DSSS) is a spread spectrum technique where the original signal is multiplied by a high-speed pseudo-random noise (PN) code. This PN code spreads the signal over a much wider bandwidth than the original signal. The receiver, knowing the PN code, can despread the signal and recover the original information.
2.1 How Does DSSS Work Step-by-Step?
Here’s a step-by-step explanation of how DSSS works:
- PN Code Generation: A pseudo-random noise (PN) code, which is a sequence of 1s and 0s that appears random but is actually deterministic, is generated.
- Spreading: The original signal is multiplied by the PN code. This process, known as spreading, increases the bandwidth of the signal.
- Transmission: The spread signal is transmitted over the air.
- Reception: The receiver receives the spread signal, which appears as noise to unintended receivers.
- Despreading: The receiver multiplies the received signal by the same PN code, synchronized with the transmitter. This process, known as despreading, recovers the original signal.
- Filtering: The despread signal is filtered to remove any remaining noise and interference.
2.2 What Are the Advantages and Disadvantages of DSSS?
Advantages of DSSS:
- High Resistance to Interference: DSSS is highly resistant to narrowband interference because the interference is spread along with the signal.
- Security: The use of a PN code makes it difficult for unauthorized users to intercept the signal.
- CDMA Capability: DSSS can be used to implement CDMA, allowing multiple users to share the same frequency band.
Disadvantages of DSSS:
- Complexity: DSSS systems are more complex to implement than narrowband systems.
- Bandwidth Intensive: Requires a large bandwidth.
- PN Code Synchronization: Requires precise synchronization of the PN code at the receiver.
2.3 What Are Some Real-World Applications of DSSS?
DSSS is used in various real-world applications, including:
- Global Positioning System (GPS): GPS uses DSSS to provide accurate positioning information.
- Wireless LANs (IEEE 802.11): Some early Wi-Fi standards used DSSS for wireless communication.
- Military Communications: DSSS is used in military communications to provide secure and reliable communication.
- CDMA Cellular Systems: CDMA cellular systems use DSSS to allow multiple users to share the same frequency band.
3. Frequency Hopping Spread Spectrum (FHSS): An Overview
Frequency Hopping Spread Spectrum (FHSS) is another spread spectrum technique where the transmission frequency is rapidly switched or “hopped” among many different frequencies. The sequence of frequencies is determined by a pseudo-random code known to both the transmitter and receiver. This makes it difficult for unauthorized users to intercept or jam the signal.
3.1 How Does FHSS Differ From DSSS?
While both FHSS and DSSS are spread spectrum techniques, they differ in how they spread the signal. DSSS spreads the signal over a wide bandwidth using a PN code, while FHSS spreads the signal by rapidly changing the transmission frequency. Here’s a comparison:
| Feature | DSSS | FHSS |
|---|---|---|
| Spreading Method | Spreads the signal using a PN code | Hops the transmission frequency |
| Bandwidth Usage | Requires a wide bandwidth | Uses multiple narrow bandwidths |
| Complexity | More complex in terms of signal processing | More complex in terms of frequency control |
| Synchronization | Requires precise PN code synchronization | Requires frequency hopping synchronization |
| Interference | Highly resistant to narrowband interference | Avoids interference by hopping frequencies |
3.2 What Are the Key Components of an FHSS System?
An FHSS system consists of several key components:
- Frequency Synthesizer: Generates the different carrier frequencies used for hopping.
- Hopping Sequence Generator: Generates the pseudo-random sequence of frequencies.
- Transmitter: Modulates and transmits the signal at the current frequency.
- Receiver: Tunes to the correct frequency at the correct time to receive the signal.
- Synchronization Mechanism: Ensures that the transmitter and receiver are synchronized to the same hopping sequence.
3.3 What Are the Advantages and Disadvantages of FHSS?
Advantages of FHSS:
- Interference Avoidance: FHSS can avoid interference by hopping to a different frequency when interference is detected.
- Jamming Resistance: It is difficult for jammers to follow the hopping sequence and jam the signal.
- Simplicity: Simpler signal processing compared to DSSS.
Disadvantages of FHSS:
- Slower Data Rates: FHSS typically supports lower data rates than DSSS.
- Synchronization Complexity: Requires precise synchronization between the transmitter and receiver.
- Frequency Hopping Overhead: The time spent hopping between frequencies can reduce the effective data rate.
3.4 What Are Some Common Applications of FHSS?
FHSS is used in various applications, including:
- Bluetooth: Bluetooth uses FHSS to minimize interference and provide reliable wireless communication.
- Military Communications: FHSS is used in military communications to provide secure and jam-resistant communication.
- Wireless Sensor Networks: FHSS is used in wireless sensor networks to avoid interference and extend battery life.
- Amateur Radio: FHSS is used by amateur radio operators for its robustness and resistance to interference.
4. Time Hopping Spread Spectrum (THSS) Explained
Time Hopping Spread Spectrum (THSS) is a spread spectrum technique where the signal is transmitted in short bursts at pseudo-random intervals. The timing of these bursts is determined by a pseudo-random code known to both the transmitter and receiver. This makes it difficult for unauthorized users to intercept the signal, as they would need to know the exact timing of the bursts.
4.1 How Does THSS Work?
Here’s how THSS works:
- Time Slot Allocation: The available time is divided into slots.
- Hopping Sequence Generation: A pseudo-random code determines the sequence of time slots in which the signal will be transmitted.
- Transmission: The signal is transmitted in short bursts during the selected time slots.
- Reception: The receiver, knowing the hopping sequence, listens for the signal during the correct time slots.
- Signal Reconstruction: The received bursts are combined to reconstruct the original signal.
4.2 What Are the Advantages and Disadvantages of THSS?
Advantages of THSS:
- Security: The pseudo-random timing of the bursts makes it difficult to intercept the signal.
- Interference Resistance: THSS can avoid interference by transmitting during time slots that are free from interference.
- Flexibility: THSS can be combined with other spread spectrum techniques to further enhance performance.
Disadvantages of THSS:
- Complexity: THSS systems can be complex to implement, requiring precise timing and synchronization.
- Lower Data Rates: The need to transmit in short bursts can limit the achievable data rates.
- Synchronization Challenges: Maintaining synchronization between the transmitter and receiver can be challenging.
4.3 Where Is THSS Commonly Used?
THSS is used in niche applications where security and interference resistance are critical, such as:
- Secure Communications: THSS is used in secure communication systems to protect sensitive information.
- Military Applications: THSS is used in military applications to provide secure and jam-resistant communication.
- Specialized Wireless Networks: THSS can be used in specialized wireless networks where interference is a concern.
5. Chirp Spread Spectrum (CSS): A Modern Approach
Chirp Spread Spectrum (CSS) is a spread spectrum technique that uses chirp signals, which are signals whose frequency increases or decreases over time. CSS is particularly well-suited for low-power, long-range communication applications.
5.1 What Is a Chirp Signal?
A chirp signal, also known as a sweep signal, is a signal in which the frequency increases or decreases linearly with time. Chirp signals are characterized by their bandwidth and chirp rate, which is the rate at which the frequency changes.
5.2 How Does CSS Work?
Here’s how CSS works:
- Chirp Signal Generation: The transmitter generates a chirp signal with a specific bandwidth and chirp rate.
- Modulation: The data is modulated onto the chirp signal.
- Transmission: The modulated chirp signal is transmitted over the air.
- Reception: The receiver receives the chirp signal and performs dechirping, which is the process of compressing the chirp signal into a narrow pulse.
- Demodulation: The data is demodulated from the compressed pulse.
5.3 What Are the Advantages and Disadvantages of CSS?
Advantages of CSS:
- Long Range Communication: CSS is capable of achieving long-range communication with low power consumption.
- Robustness: CSS is robust to multipath fading and interference.
- Simplicity: CSS systems can be relatively simple to implement.
Disadvantages of CSS:
- Lower Data Rates: CSS typically supports lower data rates than other spread spectrum techniques.
- Sensitivity to Doppler Shift: CSS can be sensitive to Doppler shift, which can occur when the transmitter and receiver are moving relative to each other.
5.4 Where Is CSS Used?
CSS is used in various applications, including:
- Low-Power Wireless Sensor Networks: CSS is used in low-power wireless sensor networks for its long-range capabilities.
- Internet of Things (IoT): CSS is used in IoT devices for its low power consumption and robustness.
- Remote Monitoring: CSS is used in remote monitoring applications, such as environmental monitoring and asset tracking.
6. M-Sequences: The Building Blocks of PN Codes
M-sequences, or maximum length sequences, are fundamental in generating pseudo-random noise (PN) codes used in spread spectrum techniques like DSSS. These sequences appear random but are deterministically generated, making them predictable for authorized receivers while remaining noise-like to others.
6.1 What Are M-Sequences?
M-sequences are binary sequences generated using linear feedback shift registers (LFSRs). They have a maximum length of 2^n – 1, where n is the number of shift registers. M-sequences exhibit properties that make them suitable for generating PN codes, including:
- Balance Property: Approximately equal numbers of 1s and 0s.
- Run Property: Sequences of consecutive 1s or 0s occur in predictable lengths and frequencies.
- Correlation Property: Low correlation except at zero shift.
6.2 How Are M-Sequences Generated?
M-sequences are generated using LFSRs, which consist of a series of shift registers and XOR gates. The output of certain registers is fed back into the input through XOR gates, creating a feedback loop. The initial state of the registers, along with the feedback connections, determines the generated sequence.
Example:
Consider an LFSR with 4 registers and a feedback polynomial of x^4 + x + 1. The sequence is generated as follows:
The initial state is only needed to generate exactly the same sequence of length (the only forbidden state is all zeros since the register will lock in this state).
Take for example:
The final sequence will look like this, 1 1 -1 -1 -1 1 -1 -1 1 1 -1 1 -1 1 1
After the fifteenth shift, the values on the registers will be again the starting seed.
6.3 What Are the Properties of M-Sequences?
M-sequences possess several key properties:
- Period: The sequence repeats after 2^n – 1 bits, where n is the number of registers.
- Autocorrelation: The autocorrelation function is high at zero shift and low elsewhere, making it easy to synchronize.
The formal definition of discrete autocorrelation is:
Consider the previous sequence
| 1 | 1 | -1 | -1 | -1 | 1 | -1 | -1 | 1 | 1 | -1 | 1 | -1 | 1 | 1 |
|---|
If we perform the following operation: = 15 which is multiply each value by itself and add them all ().
Now take ,
Performing the same operation:
= -1 =
This is the autocorrelation for each shift point. If we take them all and plot them so that there are 15 points before 0 and 15 after:
a) b)
6.4 How Are M-Sequences Used in Spread Spectrum?
M-sequences are used as PN codes in DSSS systems. The M-sequence is multiplied with the original signal to spread it over a wide bandwidth. At the receiver, the same M-sequence is used to despread the signal, recovering the original information. The low cross-correlation properties of M-sequences also allow for multiple users to share the same frequency band using CDMA.
7. Gold Sequences: Expanding the PN Code Repertoire
Gold sequences are another type of PN code used in spread spectrum systems. They are generated by combining two m-sequences, providing a larger set of unique codes compared to using m-sequences alone.
7.1 What Are Gold Sequences?
Gold sequences are created by XORing two m-sequences generated from preferred pairs of polynomials. This combination results in a new sequence with good correlation properties, suitable for CDMA applications.
7.2 How Are Gold Sequences Generated?
Gold sequences are generated using two m-sequences from preferred pairs of polynomials. For example, take the polynomials and :
Remember m-sequences gave only one sequence of length. By combining two of these sequences, we can obtain up to 31 () plus the two m-sequences themselves, generate 33 sequences (each one length) that can be used to spread different input messages (different users CDMA).
7.3 What Are the Advantages of Using Gold Sequences?
Gold codes offer several advantages:
- Larger Code Set: Generate more unique sequences compared to m-sequences.
- Good Correlation Properties: Balanced sequences with good cross-correlation properties for CDMA.
- Ease of Generation: Relatively simple to generate using preferred pairs of m-sequences.
7.4 How Are Gold Sequences Used in CDMA Systems?
Gold sequences are used in CDMA systems to provide multiple unique codes for different users. Each user is assigned a unique Gold sequence, allowing them to transmit simultaneously without interfering with each other. The receiver correlates the received signal with the appropriate Gold sequence to extract the desired user’s data.
8. Walsh-Hadamard Sequences: Orthogonality for Multiple Access
Walsh-Hadamard sequences are orthogonal codes used in CDMA systems. Their orthogonality ensures that signals from different users do not interfere with each other, providing efficient multiple access capabilities.
8.1 What Are Walsh-Hadamard Sequences?
Walsh-Hadamard sequences are sets of orthogonal binary sequences. Orthogonality means that the cross-correlation between any two different sequences in the set is zero. These sequences are typically represented as rows of a Hadamard matrix.
8.2 How Are Walsh-Hadamard Sequences Generated?
Walsh-Hadamard sequences are generated using a Hadamard matrix defined for as:
For larger matrices use the recursion:
Example for
8.3 What Are the Advantages of Using Walsh Codes?
Walsh codes offer significant advantages:
- Orthogonality: Ensures zero interference between users in a synchronous CDMA system.
- Simple Generation: Easy to generate using the Hadamard matrix.
- Efficient Multiple Access: Allows for efficient multiple access in CDMA systems.
8.4 How Are Walsh-Hadamard Sequences Used in CDMA Systems?
Walsh-Hadamard sequences are used in CDMA systems to assign unique orthogonal codes to different users. Each user’s signal is spread using their assigned Walsh code. Due to the orthogonality of the codes, the receiver can perfectly separate the signals from different users, provided they are synchronized.
9. Spreading and Despreading: The Core Processes
Spreading and despreading are the fundamental processes in spread spectrum communication. Spreading increases the bandwidth of the transmitted signal, while despreading recovers the original signal at the receiver.
9.1 What Is Spreading?
Spreading is the process of increasing the bandwidth of a signal by multiplying it with a PN code. This process reduces the power spectral density of the signal, making it more resistant to interference and harder to detect.
The block diagram of the DSSS communication system for QPSK is presented in Figure 6. Notice that the PN sequence is introduced here to both in-phase (I) and quadrature (Q) components.
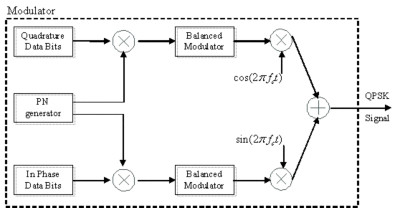 Block diagram of the spread spectrum QPSK modulator
Block diagram of the spread spectrum QPSK modulator
The sequence should be long enough (with respect to the message signal) to have the noise-like spectrum. This is the relation between spreading sequence rate and message rate : In practical systems, is an integer number and it is the number of phase shift of the PN sequence for each message bit. For example, for GPS systems N = 1024.
Figure 7: Spreading the message, each bit of the message will contain the entire PN sequence
9.2 How Does Spreading Work?
The original message has now and therefore The output combined baseband sequence is: Where is the sent baseband waveform, is the PN waveform and is the bit sequence.
9.3 What Is Despreading?
Despreading is the reverse process of spreading. At the receiver, the received signal is multiplied by the same PN code used for spreading. This process collapses the spread signal back into its original bandwidth, recovering the original information.
9.4 How Does Despreading Work?
Received baseband waveform is the combination of the transmitted waveform and noise in the channel.
The received signal will be combined again with the spreading sequence. Notice that the noise is also going to be processed on the same procedure but correlation properties will not increase the noise power.
The received signal will be the combination of the transmitted signal plus noise:
We can substitute the sent waveform by the combination of the PN sequence and the bit sequence. The modulator will multiply it by the PN sequence:
If is synchronized, and is like multiplying noise times noise which gives other kind of noise (similar in amplitude). Consider the ideal example from Figure 9.
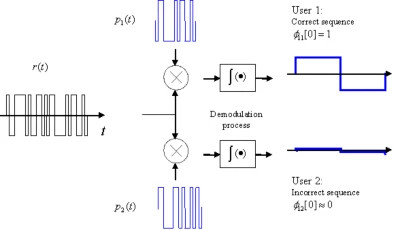 diagram of original signal for two users
diagram of original signal for two users
Figure 9: Recuperate original signal for two different users. User 1 has the correct sequence. User 2 has different sequence and therefore the output message will have many errors (no information)
9.5 Why Are Spreading and Despreading Important?
Spreading and despreading are crucial for the functionality of spread spectrum systems. They provide:
- Interference Resistance: By spreading the signal, the impact of narrowband interference is reduced.
- Security: The spread signal is harder to detect and intercept.
- CDMA Capability: Allows multiple users to share the same frequency band.
10. Spread Spectrum in Modern Wireless Communication
Spread spectrum technology continues to play a crucial role in modern wireless communication systems, offering enhanced security, interference resistance, and efficient multiple access capabilities.
10.1 How Is Spread Spectrum Used in 5G?
In 5G, spread spectrum techniques are used to enhance the reliability and security of wireless communications. DSSS and FHSS, along with advanced coding schemes, help mitigate interference and provide robust connectivity in dense urban environments.
10.2 What Role Does It Play in IoT Devices?
Spread spectrum is essential for IoT devices, enabling low-power, long-range communication. CSS and other spread spectrum techniques allow IoT devices to operate reliably in noisy environments, ensuring seamless connectivity for a wide range of applications.
10.3 What Are the Future Trends for Spread Spectrum Technology?
Future trends in spread spectrum technology include:
- Advanced Coding Schemes: Development of more efficient and robust coding schemes to enhance the performance of spread spectrum systems.
- Cognitive Radio: Integration of cognitive radio techniques to dynamically adapt the spreading parameters based on the environment.
- mmWave Communication: Application of spread spectrum techniques in millimeter-wave communication systems to overcome challenges related to signal propagation.
- Quantum Spread Spectrum: Exploring the use of quantum principles to further enhance the security of spread spectrum communications.
FAQ: Understanding Spread Spectrum Technology
1. What is the main purpose of spread spectrum technology?
The main purpose of spread spectrum technology is to increase resistance to interference, jamming, and eavesdropping by spreading the signal over a wide frequency band.
2. How does spread spectrum improve security?
Spread spectrum improves security by making the signal harder to detect and intercept. The wideband nature of the signal reduces the power spectral density, making it appear as noise to unintended receivers.
3. What is the difference between DSSS and FHSS?
DSSS spreads the signal by multiplying it with a PN code, while FHSS spreads the signal by rapidly changing the transmission frequency.
4. What are M-sequences used for in spread spectrum?
M-sequences are used to generate PN codes, which are used for spreading and despreading signals in DSSS systems.
5. How do Walsh-Hadamard sequences enable multiple access in CDMA?
Walsh-Hadamard sequences are orthogonal codes that allow multiple users to transmit simultaneously without interfering with each other in CDMA systems.
6. What is the role of spreading and despreading in spread spectrum communication?
Spreading increases the bandwidth of the signal, making it more resistant to interference, while despreading recovers the original signal at the receiver.
7. What are the key advantages of using spread spectrum technology?
The key advantages include interference resistance, jamming resistance, security, CDMA capability, and multipath mitigation.
8. In what applications is chirp spread spectrum (CSS) commonly used?
CSS is commonly used in low-power wireless sensor networks, Internet of Things (IoT) devices, and remote monitoring applications.
9. How is spread spectrum technology used in 5G?
In 5G, spread spectrum techniques are used to enhance the reliability and security of wireless communications, mitigating interference and providing robust connectivity.
10. What are some future trends for spread spectrum technology?
Future trends include advanced coding schemes, cognitive radio integration, application in millimeter-wave communication, and exploration of quantum spread spectrum.
Conclusion
Spread spectrum technology is a cornerstone of modern wireless communication, providing enhanced security, interference resistance, and efficient multiple access capabilities. From DSSS and FHSS to CSS and advanced coding schemes, spread spectrum continues to evolve to meet the demands of emerging applications like 5G and IoT. At pioneer-technology.com, we are committed to providing you with the latest insights and in-depth analysis of these groundbreaking technologies.
Ready to dive deeper into the world of pioneering technologies? Visit pioneer-technology.com now to explore our comprehensive articles, detailed analyses, and cutting-edge updates. Whether you’re a student, tech professional, investor, or simply a tech enthusiast, pioneer-technology.com is your go-to resource for staying ahead in the fast-paced world of technology. Don’t miss out – discover the future today!
